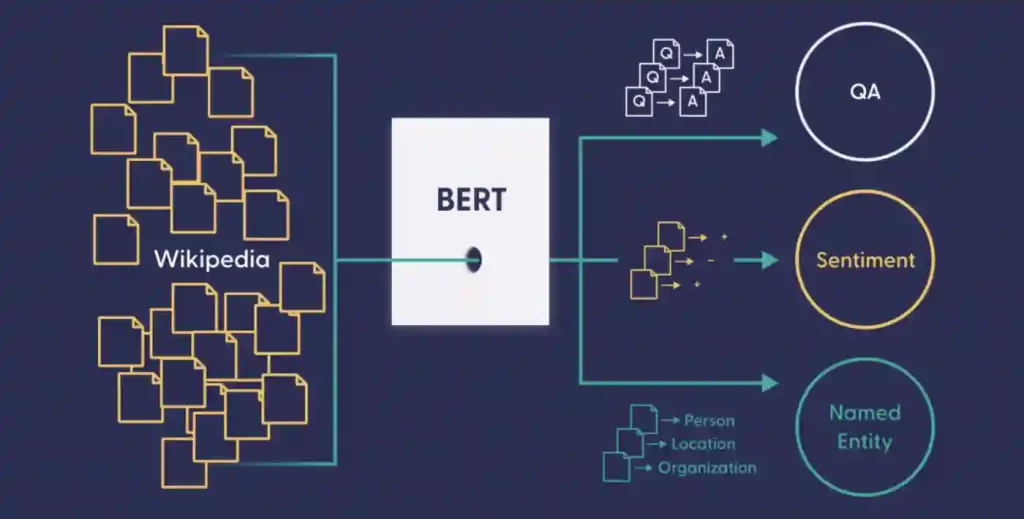
Training in Ethical Hacking Is Required

These days, operating a business or personal endeavor online comes with several inherent difficulties. People have started using other websites and accounts to alter crucial data as well as sneak in and gather information. Hacking is the name for this type of intrusion, and it must be stopped! It must be reviewed frequently to keep people out of your account. It was done by an ethical hacker. Due to this, there is a growing demand for ethical hacking training on a global scale today.
Who commits ethical hacking?
In computer jargon, persons who log into other people’s accounts with diverse purposes are known as “people with different colored hats”! The ethical hacker, in this sense, is a person who dons a white hat. A person with hacker training’s primary job is to break into or penetrate a system to assess the safety and security of the embedded IT system. White hackers are educated to break into a company’s or an individual’s computer systems that house all crucial and extremely sensitive information. They are experts in the field of computer security. It is significant to highlight that while these systems may appear to be quite safe from the outside, they are nevertheless vulnerable to challenges from dishonest tactics.
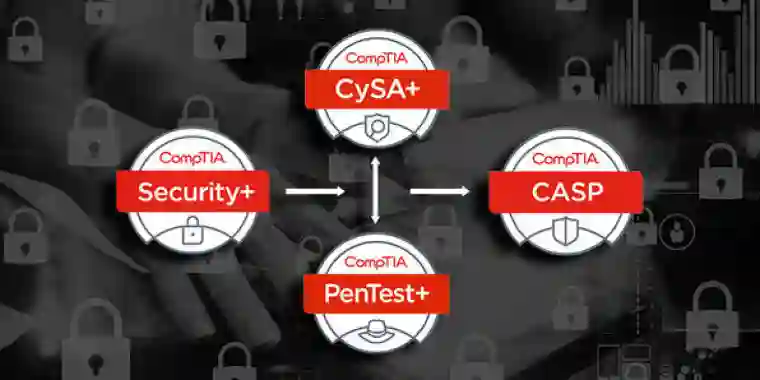
The candidates go through ethical hacking training to get ready for this activity. Businesses use either one or a group of them to test the system’s dependability. They are referred to as red or tiger teams when they collaborate. Then learn about the many ways to break into a system through ethical hacking training, and they use the techniques to sneak in and look for security weaknesses. Many companies currently provide accredited training courses for Phone hacker.
What purpose does ethical hacking training serve?
Many businesses are still unsure about the value of using ethical hacking to check into their systems. They believe that nobody would attempt to break into their system. The corporation could lose millions as a result of ignorance. However, if the system is not examined by a professional and the data is hacked by the incorrect individuals, highly essential and crucial information may leak out and end up in the hands of the incorrect individuals. As a result, it’s crucial to either hire a professional who has completed certified ethical hacker training or provide in-house staff with hacker training. These people assist in identifying and fixing systemic issues and safeguarding data from improper usage.
But how do you suppose your staff would react if they learned that all other employees had access to private information about their employment? The issue of trust that is progressively developed between a firm and its employees would be blown out of the water by one single email, so you would have some substantial damage control to undertake.
Many individuals think all they need to do is make sure their customers’ information is secure and that their payment information (if the business conducts transactions online) isn’t compromised, but the example above demonstrates that’s not the case. Getting outside assistance is frequently a smart move because hackers can harm your company in more ways than you might imagine.
So, to whom do you turn? In other words, you should concentrate on hiring a reputable company with a strong track record in internet security. This kind of company has all the information and expertise necessary to shield you from hackers of all stripes, available round-the-clock.
When left open to hackers, these dishonest individuals also access employee files and upload viruses into the system, which has the potential to crash and ruin the entire network. The after-effects of such a kind of hacking could result in the loss of vital and classified information. Because they wouldn’t trust the business with sensitive information, many of the company’s customers might leave. These are a few of the factors that make hiring individuals who have taken ethical hacking training crucial for the success of the business and the well-being of the workforce. Your IT health is ultimately in your control.